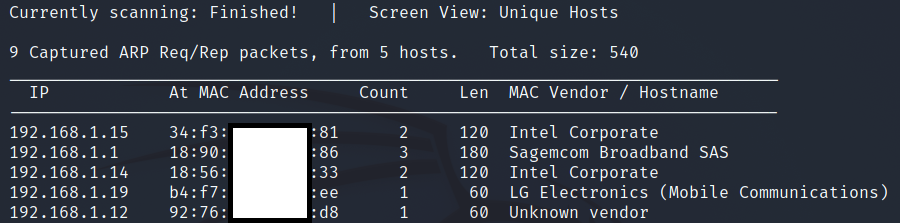
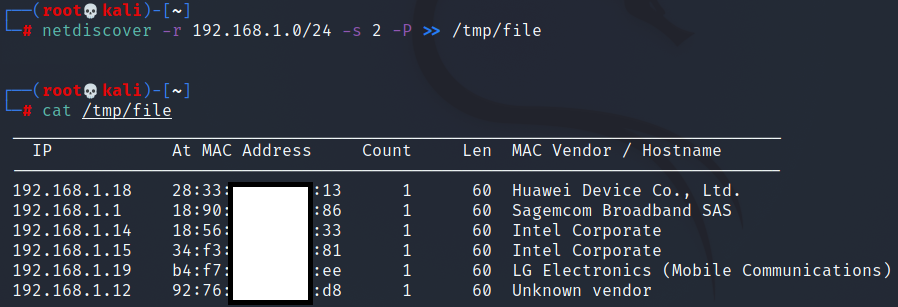
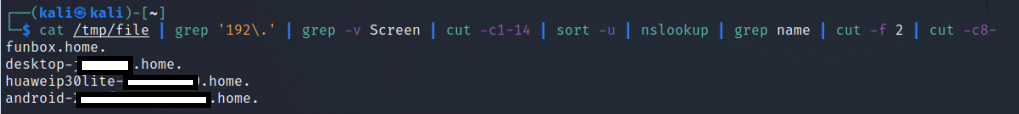
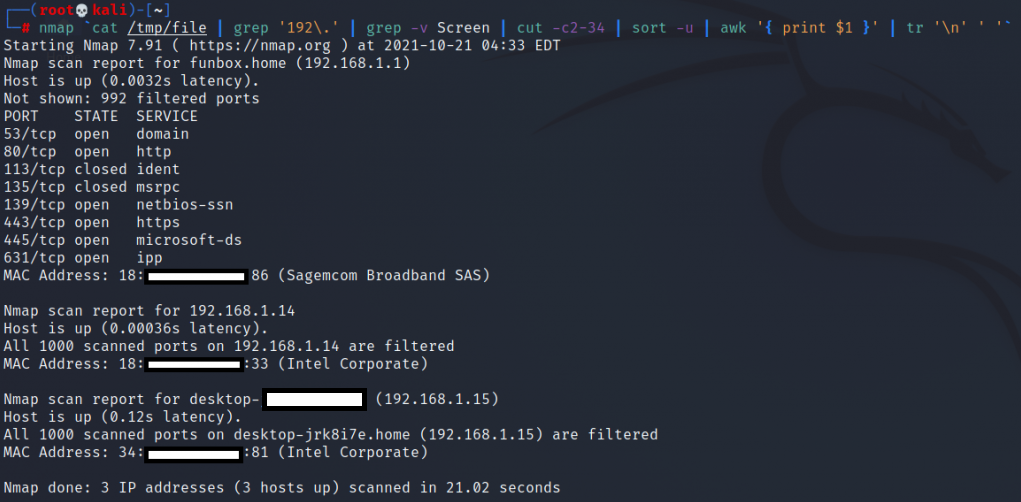
iftop is a command-line tool used for real-time network bandwidth monitoring. It displays a continuously updated list of network connections and the amount of data transferred between them. The connections are listed in a table format and are sorted by either the amount of data transferred or the total number of packets sent or received.
iftop provides a variety of filtering options, allowing you to limit the display to specific hosts, networks, or ports. It also provides support for IPv6, and it can display information about the source and destination IP addresses, port numbers, and protocols.
iftop is particularly useful for monitoring network traffic in real-time and identifying which applications or services are consuming the most bandwidth. It can also help identify network performance issues and can assist in troubleshooting network problems.
Overall, iftop is a powerful and flexible tool for network monitoring and analysis, and it can be a valuable addition to any network administrator’s toolkit.
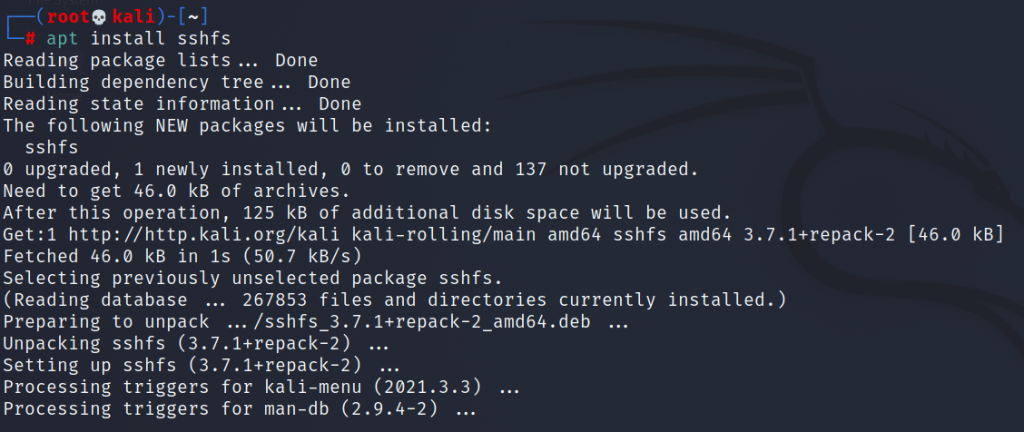
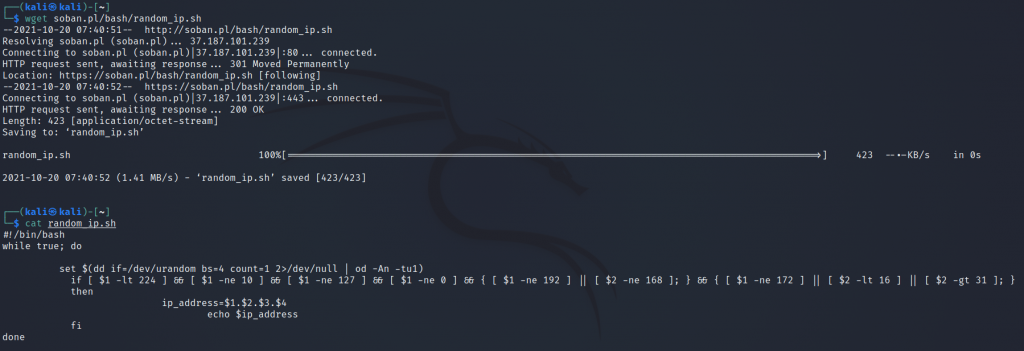
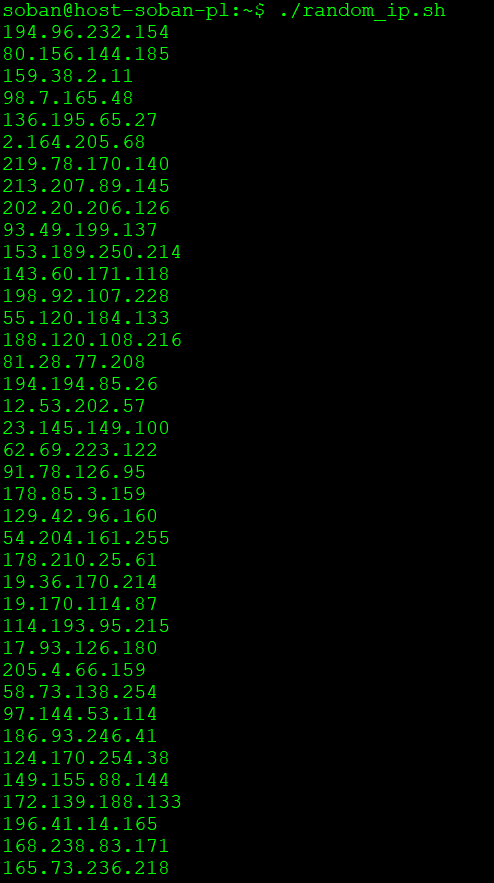
One of the more useful network traffic monitoring tools I find is iftop. It is especially useful when the link’s throat is flooded. In my experience, it is easy to use it to catch all kinds of network attacks, especially DoS. In the example given below, I will send a larger file to the remote machine and limit its upload speed, in the meantime I will observe the traffic with the iftop tool. Let’s start by installing iftop on the local machine. In this case it is kali linux:
|
1 |
# apt install iftop |
The distribution doesn’t matter in this case, just like it installs on any other operating system, it may well be linux debian.
We will do the same on the remote machine, so let’s move on to installing iftop on linux debian:
|
1 |
# apt install iftop |
To start monitoring network traffic, run iftop with parameters: ‘-PpNn’:
|
1 |
# iftop -PpNn |
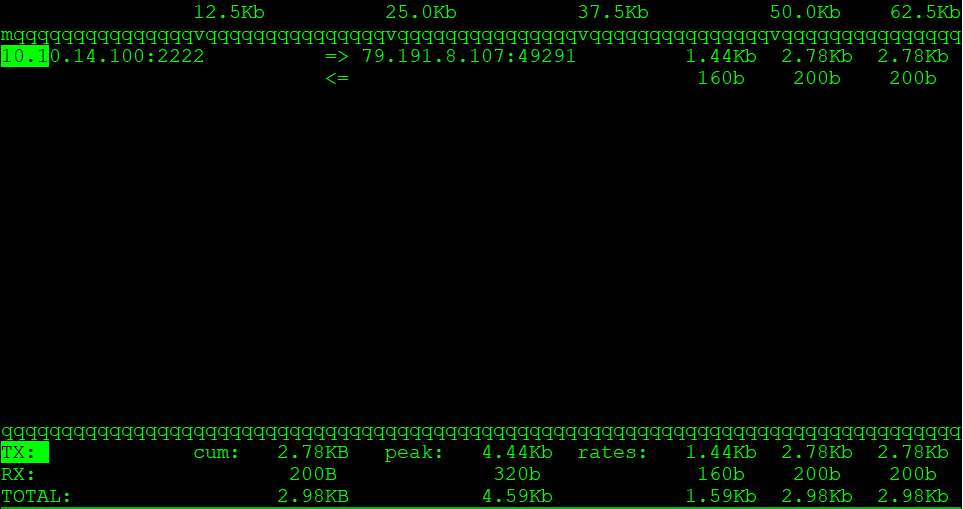
As I am ssh connected to the remote machine, I can see my network connection.
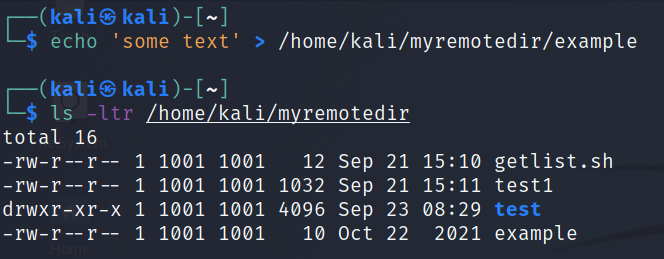
Now let’s go back to the local machine, create a large file:
|
1 |
# truncate -s 1G 1G-file.txt |
Once we have created a 1GB file, let’s try to send it with a transfer limit to the remote machine:
|
1 |
# scp -l 800 -P2222 1G-file.txt soban@soban.pl:~ |
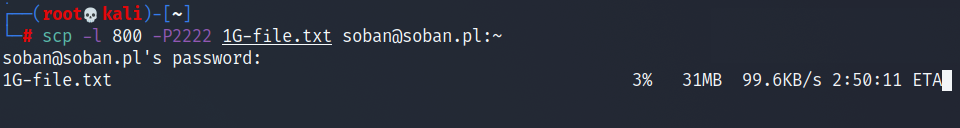
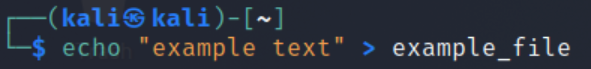
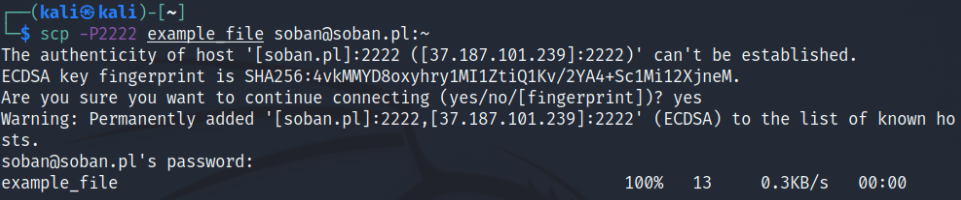
In this case, I used scp with the limit of 800 to send the file. To calculate how many KB/sec this is, divide by 8. From a simple calculation it follows that 800/8 = 100. To see scp and how to send files I encourage you to read: Securely Copy Files (scp) tool to copying files by ssh.
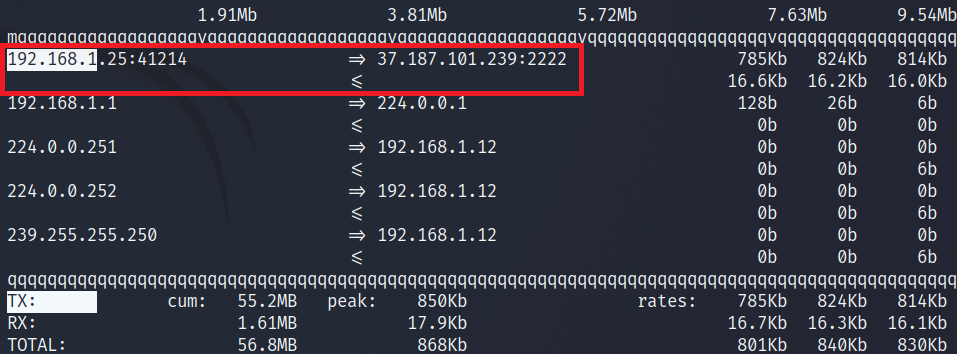
When sending the file, the traffic on the local machine looked like this (outgoing traffic):
|
1 |
# iftop -PpNn |
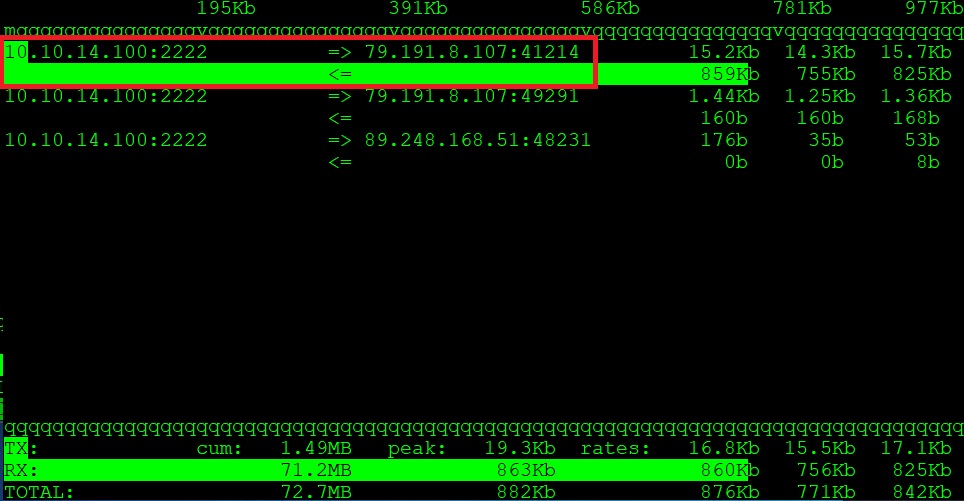
At the same time, it looked like this on the remote machine (incoming traffic):
|
1 |
# iftop -PpNn |
As you can see, in this way you can catch both outgoing and incoming traffic. The iftop tool has more parameters, I encourage you to read the manual. It is a simple tool, however, thanks to it, we can easily observe live network traffic. In the case of bruteforce, a significant number of connections will be made, but in the case of a DoS attack, the attacker will try to saturate the bandwidth, therefore the incoming traffic on the machine will be large. There are situations when the machine is naturally overloaded with the network, then you should limit the connection speed, in this case iptables works perfectly.