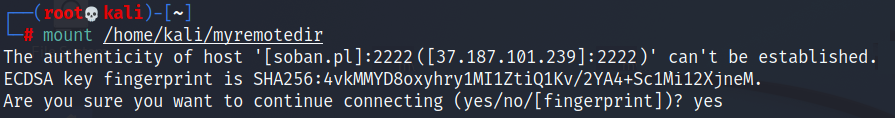
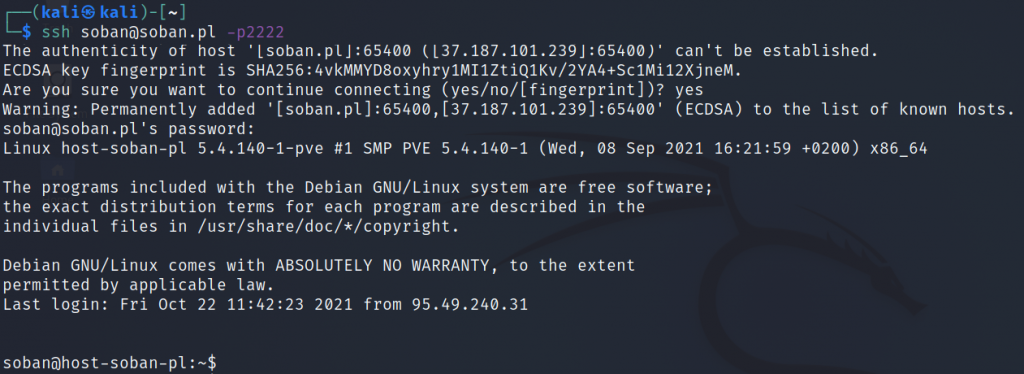
Nowadays, many bots or hackers look for port 22 on servers and try to log in. Usually, the login attempt is made as the standard linuxe root user. In this short article, I will describe how to create a user that will be able to log in as root and change the default ssh port 22 to 2222. Let’s go:
|
1 |
useradd -m soban -s /bin/bash |
This way we created the user ‘soban’ and assigned it the default shell ‘/bin/bash’.
We still need to set a password for the user ‘soban’:
|
1 |
# passwd soban |
In the next step, let’s add it to ‘/etc/sudoers’ so that it can become root. Keep in mind that once the user can get root, he will be able to do anything on the machine!
|
1 |
# vi /etc/sudoers |
Please add this entry below:
|
1 2 |
#user can made sudo on root (sudo su -) soban ALL=(ALL) NOPASSWD: ALL |
How can we test whether the user has the ability to log in as root? Nothing easier, first we’ll switch to the user we just created:
|
1 |
# su - soban |
To list the possible sudo commands, just type the command:
|
1 |
$ sudo -l |
Finally, to confirm whether it is possible to log in as root, you should issue the command:
|
1 |
# sudo su - |
Now that we have a root user ready, let’s try disabling ssh logon directly and change the default port. To do this, go to the default configuration of the ssh service, which is located in ‘/etc/ssh/sshd_config’:
|
1 |
# vi /etc/ssh/sshd_config |
We are looking for a line containing ‘Port’ – it can be hashed, so it should be unhashed and ‘PermitRootLogin’. Then set them as below:
|
1 2 |
Port 2222 PermitRootLogin no |
In this way, we changed the default port 22 to 2222 and disallowed the possibility of logging in directly to the root user. However, the ssh service still needs to be reloaded, in debian or kali linux we do it like this:
|
1 |
# service sshd restart |
In this way, we have managed to create a user who can safely log into the ssh service and become root. In addition, after changing the port, we will not go out on port 22 scans, which by default is set and scanned by a potential burglar. Installing the fail2ban service is also a very good improvement in security.