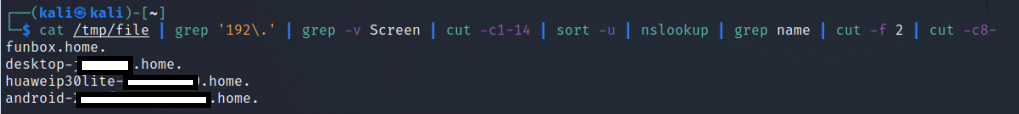
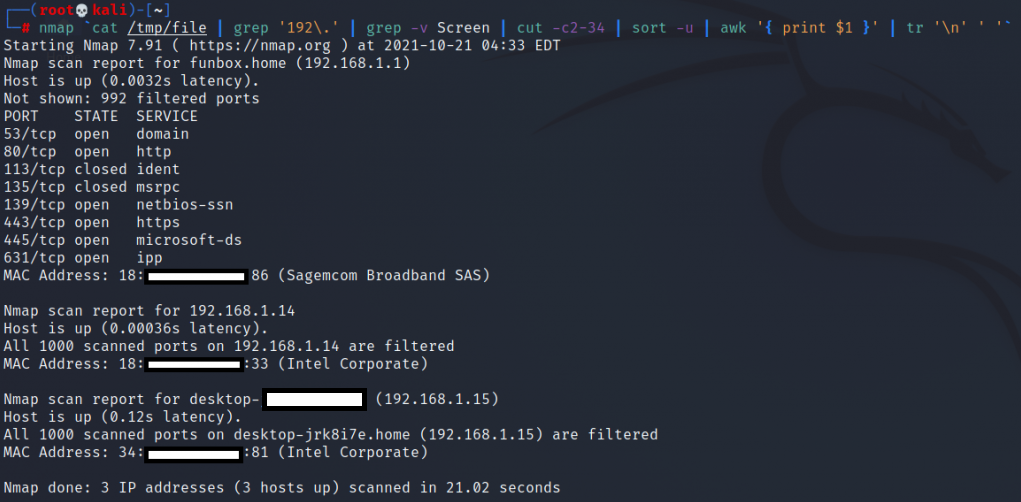
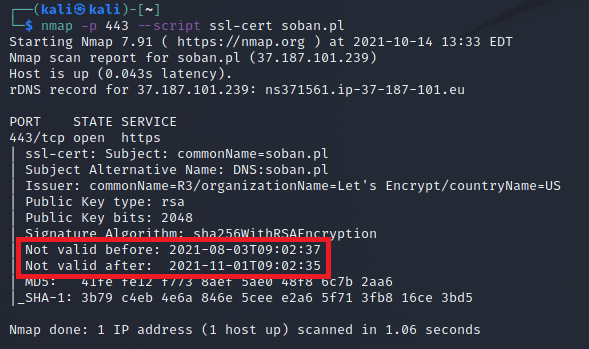
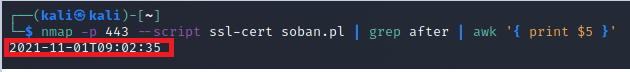
~# nmap -sV --script ssl-enum-ciphers -p 443 google.com
Starting Nmap 7.80 ( https://nmap.org ) at 2021-09-30 09:58 CEST
Nmap scan report for google.com (142.250.179.78)
Host is up (0.0045s latency).
Other addresses for google.com (not scanned): 2a00:1450:4007:80c::200e
rDNS record for 142.250.179.78: par21s19-in-f14.1e100.net
PORT STATE SERVICE VERSION
443/tcp open ssl/https gws
| fingerprint-strings:
| GetRequest:
| HTTP/1.0 200 OK
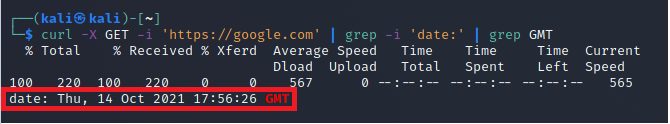
| Date: Thu, 30 Sep 2021 07:58:20 GMT
| Expires: -1
| Cache-Control: private, max-age=0
| Content-Type: text/html; charset=ISO-8859-1
| P3P: CP="This is not a P3P policy! See g.co/p3phelp for more info."
| Server: gws
| X-XSS-Protection: 0
| X-Frame-Options: SAMEORIGIN
| Set-Cookie: CONSENT=PENDING+585; expires=Fri, 01-Jan-2038 00:00:00 GMT; path=/; domain=.google.com; Secure
| Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000,h3-T051=":443"; ma=2592000,h3-Q050=":443"; ma=2592000,h3-Q046=":443"; ma=2592000,h3-Q043=":443"
; ma=2592000,quic=":443"; ma=2592000; v="46,43"
| Accept-Ranges: none
| Vary: Accept-Encoding
| <!doctype html><html itemscope="" itemtype="http://schema.org/WebPage" lang="fr"><head><meta content="text/html; charset=UTF-8" http-equiv="Content-Typ
e"><meta content="/images/branding/googleg/1x/googleg_standard_color_128dp.png" itemprop="image"><title>Google</titl
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: GET, HEAD
| Date: Thu, 30 Sep 2021 07:58:21 GMT
| Content-Type: text/html; charset=UTF-8
| Server: gws
| Content-Length: 1592
| X-XSS-Protection: 0
| X-Frame-Options: SAMEORIGIN
| Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000,h3-T051=":443"; ma=2592000,h3-Q050=":443"; ma=2592000,h3-Q046=":443"; ma=2592000,h3-Q043=":443"
; ma=2592000,quic=":443"; ma=2592000; v="46,43"
| <!DOCTYPE html>
| <html lang=en>
| <meta charset=utf-8>
| <meta name=viewport content="initial-scale=1, minimum-scale=1, width=device-width">
| <title>Error 405 (Method Not Allowed)!!1</title>
| <style>
|_ *{margin:0;padding:0}html,code{font:15px/22px arial,sans-serif}html{background:#fff;color:#222;padding:15px}body{margin:7% auto 0;max-width:390px;min-h
eight:180px;padding:30px 0 15px}* > body{background:url(//www.google.com/images/errors/robot.png) 100% 5px no-repeat;padding-righ
|_http-server-header: gws
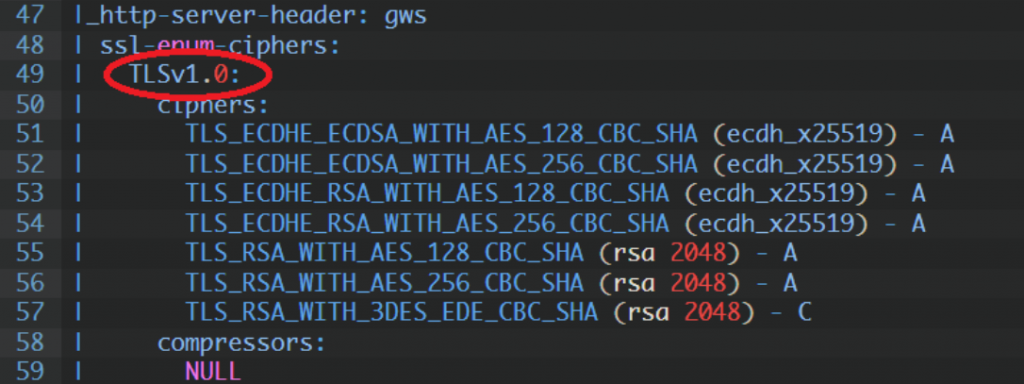
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
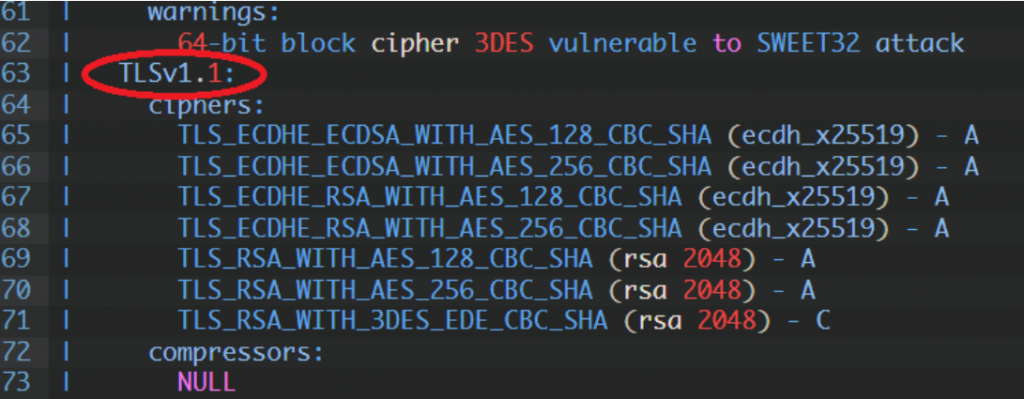
| TLSv1.1:
| ciphers:
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
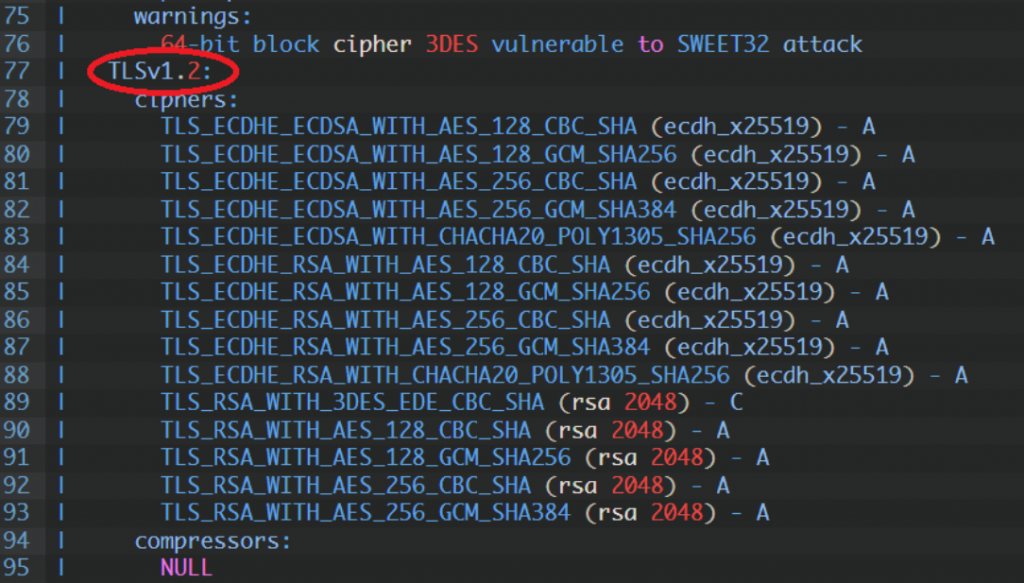
| TLSv1.2:
| ciphers:
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| compressors:
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
|_ least strength: C
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cg
i?new-service :
SF-Port443-TCP:V=7.80%T=SSL%I=7%D=9/30%Time=61556E1D%P=x86_64-pc-linux-gnu
SF:%r(GetRequest,4C58,"HTTP/1\.0\x20200\x20OK\r\nDate:\x20Thu,\x2030\x20Se
SF:p\x202021\x2007:58:20\x20GMT\r\nExpires:\x20-1\r\nCache-Control:\x20pri
SF:vate,\x20max-age=0\r\nContent-Type:\x20text/html;\x20charset=ISO-8859-1
SF:\r\nP3P:\x20CP=\"This\x20is\x20not\x20a\x20P3P\x20policy!\x20See\x20g\.
SF:co/p3phelp\x20for\x20more\x20info\.\"\r\nServer:\x20gws\r\nX-XSS-Protec
SF:tion:\x200\r\nX-Frame-Options:\x20SAMEORIGIN\r\nSet-Cookie:\x20CONSENT=
SF:PENDING\+585;\x20expires=Fri,\x2001-Jan-2038\x2000:00:00\x20GMT;\x20pat
SF:h=/;\x20domain=\.google\.com;\x20Secure\r\nAlt-Svc:\x20h3=\":443\";\x20
SF:ma=2592000,h3-29=\":443\";\x20ma=2592000,h3-T051=\":443\";\x20ma=259200
SF:0,h3-Q050=\":443\";\x20ma=2592000,h3-Q046=\":443\";\x20ma=2592000,h3-Q0
SF:43=\":443\";\x20ma=2592000,quic=\":443\";\x20ma=2592000;\x20v=\"46,43\"
SF:\r\nAccept-Ranges:\x20none\r\nVary:\x20Accept-Encoding\r\n\r\n<!doctype
SF:\x20html><html\x20itemscope=\"\"\x20itemtype=\"http://schema\.org/WebPa
SF:ge\"\x20lang=\"fr\"><head><meta\x20content=\"text/html;\x20charset=UTF-
SF:8\"\x20http-equiv=\"Content-Type\"><meta\x20content=\"/images/branding/
SF:googleg/1x/googleg_standard_color_128dp\.png\"\x20itemprop=\"image\"><t
SF:itle>Google</titl")%r(HTTPOptions,7D7,"HTTP/1\.0\x20405\x20Method\x20No
SF:t\x20Allowed\r\nAllow:\x20GET,\x20HEAD\r\nDate:\x20Thu,\x2030\x20Sep\x2
SF:02021\x2007:58:21\x20GMT\r\nContent-Type:\x20text/html;\x20charset=UTF-
SF:8\r\nServer:\x20gws\r\nContent-Length:\x201592\r\nX-XSS-Protection:\x20
SF:0\r\nX-Frame-Options:\x20SAMEORIGIN\r\nAlt-Svc:\x20h3=\":443\";\x20ma=2
SF:592000,h3-29=\":443\";\x20ma=2592000,h3-T051=\":443\";\x20ma=2592000,h3
SF:-Q050=\":443\";\x20ma=2592000,h3-Q046=\":443\";\x20ma=2592000,h3-Q043=\
SF:":443\";\x20ma=2592000,quic=\":443\";\x20ma=2592000;\x20v=\"46,43\"\r\n
SF:\r\n<!DOCTYPE\x20html>\n<html\x20lang=en>\n\x20\x20<meta\x20charset=utf
SF:-8>\n\x20\x20<meta\x20name=viewport\x20content=\"initial-scale=1,\x20mi
SF:nimum-scale=1,\x20width=device-width\">\n\x20\x20<title>Error\x20405\x2
SF:0\(Method\x20Not\x20Allowed\)!!1</title>\n\x20\x20<style>\n\x20\x20\x20
SF:\x20\*{margin:0;padding:0}html,code{font:15px/22px\x20arial,sans-serif}
SF:html{background:#fff;color:#222;padding:15px}body{margin:7%\x20auto\x20
SF:0;max-width:390px;min-height:180px;padding:30px\x200\x2015px}\*\x20>\x2
SF:0body{background:url\(//www\.google\.com/images/errors/robot\.png\)\x20
SF:100%\x205px\x20no-repeat;padding-righ");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 67.76 seconds