Netcat, also known as “nc,” is a versatile networking tool that is commonly used in Linux and other Unix-like operating systems. It is a command-line utility that can be used for various network-related tasks, such as port scanning, file transfer, and even as a lightweight web server.
The primary function of Netcat is to create network connections between two hosts, allowing data to be transferred between them. It can establish a connection as a client or a server, and it supports both TCP and UDP protocols. This makes it useful for testing network services, troubleshooting network issues, and performing security assessments.
Netcat can be used to scan for open ports on a remote host, allowing system administrators to identify potential security vulnerabilities. It can also be used to transfer files between hosts, similar to the way that the “cp” command works in Linux. Additionally, it can be used to create a simple web server, allowing files to be served over HTTP.
One of the key features of Netcat is its ability to operate in both interactive and non-interactive modes. In interactive mode, it acts like a chat program, allowing users to communicate with each other in real-time. In non-interactive mode, it can be used as a background process that quietly sends or receives data without any user interaction.
Overall, Netcat is a powerful and flexible tool that can be used for a wide range of networking tasks. Its simplicity and ease of use make it a popular choice among system administrators, network engineers, and security professionals.
Sometimes network connections are blocked by various network devices. In the verification of the connection over TCP, we can use, for example, telnet. After all, before we start a server-side service like jboss, we can use a simple utility like netcat to open the port.
In this example we will be using two machines. However, one of them is “host-soban-pl” with the IP address: 10.10.14.100:
|
1 |
$ ip a |
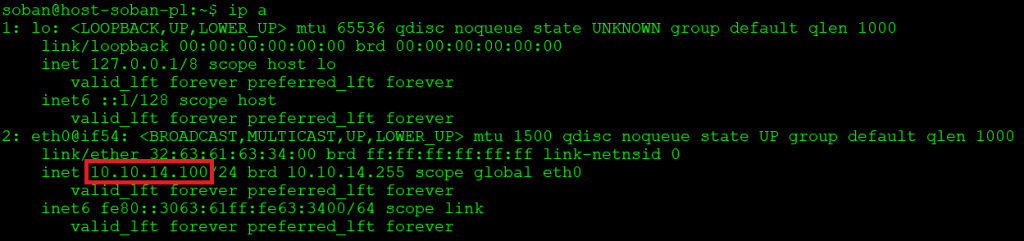
The second is “soban-pl” with the IP address: 10.10.11.105:
|
1 |
# ip a |
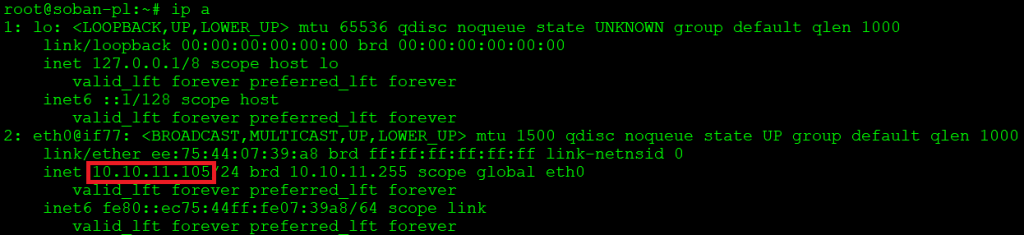
Below, for example, I will show you how to check an already open tcp connection and one that is closed. On the other side, on port 80, I have an open port with nginx:
|
1 |
$ telnet 10.10.11.105 80 |
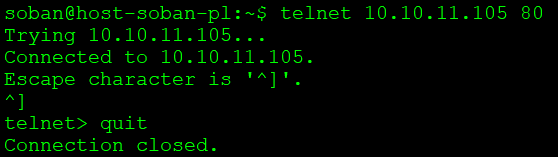
Nmap below confirms port opening, additionally identified the service as http:
|
1 |
$ nmap 10.10.11.105 -p 80 |
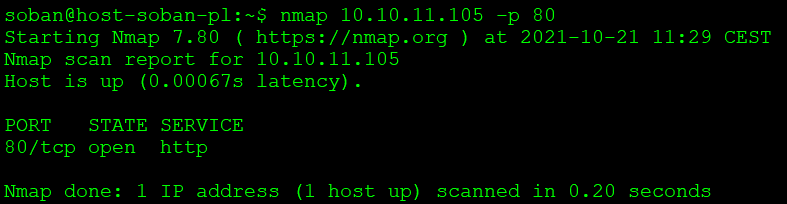
The conclusion is that the service has network transitions and you can correctly connect over TCP. Now it will try to open a connection that does not exist, e.g. on port 81.
|
1 |
$ telnet 10.10.11.105 81 |
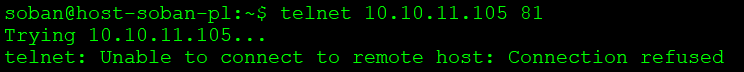
As you can see, the connection is not possible because the port is closed. The assumption is that the port may be open, but for example the firewall blocks it. Then you need to set the appropriate rules on it.
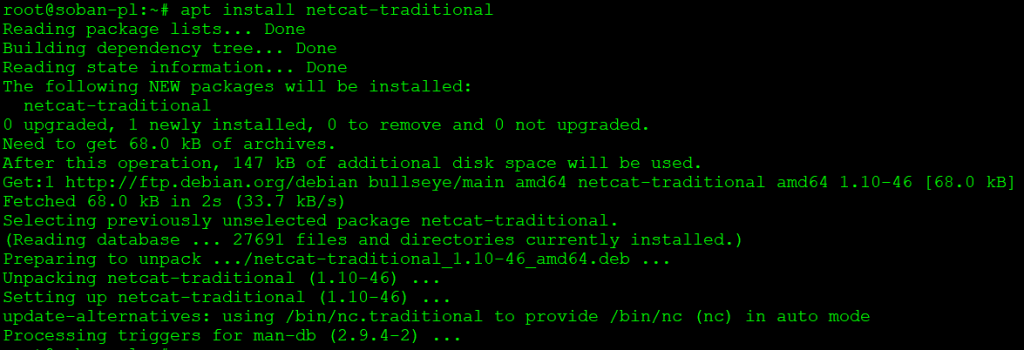
After all, in this case I know that the firewall does not block anything, so it will try to open the port with netcat. First we need to install netcat in debian, it is done like this:
|
1 |
# apt install netcat-traditional |
Now let’s move on to running netcat on port 81:
|
1 |
# netcat -l -p 81 & |
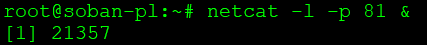
In this case, I specially gave the command ‘&’ at the end to leave the netcat process in the background. At this point, netcat is listening on port 81.
Now we can proceed to checking the correctness of the connection with the use of telnet:
|
1 |
$ telnet 10.10.11.105 81 |
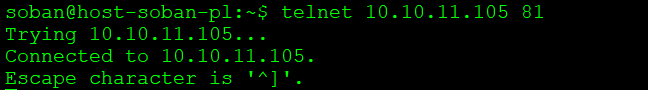
In the meantime, on the server machine, we can use the netstat tool to verify the connection and check from which machine the traffic is coming:
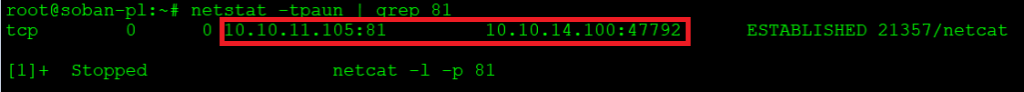
As you can see, a correct connection from the 10.10.14.100 host has been established with the server on 10.10.11.105 on port 81.
To end the call, hit ‘^]‘ (ctrl +]), then type quit and enter.
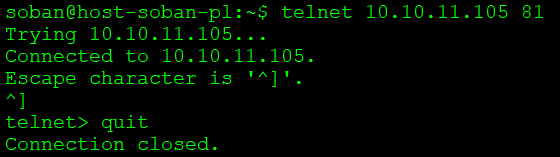
In this way, we can verify the correctness of the network connection and whether any firewall or other network problem is an obstacle to its correct establishment. Netcat is a very powerful and useful tool, you can use it to transfer files etc. Netstat is also very useful in situations where network congestion occurs and one of the hosts is attacked. It is then easy to notice that a large number of network connections are made.