SSLScan is a command-line tool used for SSL/TLS vulnerability scanning. It is used to detect SSL/TLS vulnerabilities and weaknesses on servers that use SSL/TLS. SSLScan supports all SSL and TLS protocols and cipher suites, including new ones such as TLS 1.3.
SSLScan can be used to identify various SSL/TLS vulnerabilities, such as weak ciphers and encryption algorithms, insecure renegotiation, and Heartbleed attacks. It can also identify unsupported SSL/TLS versions and protocols, as well as expired or self-signed certificates.
SSLScan works by connecting to the target server and sending a series of SSL/TLS handshake messages to determine the supported protocols and cipher suites. It then checks for vulnerabilities and weaknesses by trying various attacks against the server, such as malformed SSL/TLS packets and invalid certificates.
SSLScan can be run from the command line and supports various options and flags to customize the scan. For example, it can be used to scan a specific port, specify the SSL/TLS version, or use a specific cipher suite.
Overall, SSLScan is a useful tool for checking SSL/TLS vulnerabilities and ensuring that servers are secure. It is commonly used by security professionals and system administrators to identify and mitigate SSL/TLS vulnerabilities on their networks.
In debian 11:
|
1 2 |
# cat /etc/issue Debian GNU/Linux 11 \n \l |
One of the best tool for scaning ssl is sslscan in Linux.
You can install on debian like this as root of course:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
# apt install sslscan Reading package lists... Done Building dependency tree... Done Reading state information... Done The following NEW packages will be installed: sslscan 0 upgraded, 1 newly installed, 0 to remove and 0 not upgraded. Need to get 53.4 kB of archives. After this operation, 182 kB of additional disk space will be used. Get:1 http://ftp.debian.org/debian bullseye/main amd64 sslscan amd64 2.0.7-1 [53.4 kB] Fetched 53.4 kB in 0s (509 kB/s) Selecting previously unselected package sslscan. (Reading database ... 65077 files and directories currently installed.) Preparing to unpack .../sslscan_2.0.7-1_amd64.deb ... Unpacking sslscan (2.0.7-1) ... Setting up sslscan (2.0.7-1) ... Processing triggers for man-db (2.9.4-2) ... |
and than we can check for example google.com:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 |
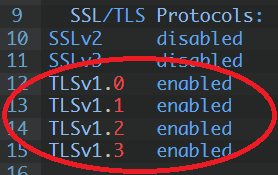
$ sslscan google.com:443 Version: 2.0.7 OpenSSL 1.1.1k 25 Mar 2021 Connected to 142.250.179.78 Testing SSL server google.com on port 443 using SNI name google.com SSL/TLS Protocols: SSLv2 disabled SSLv3 disabled TLSv1.0 enabled TLSv1.1 enabled TLSv1.2 enabled TLSv1.3 enabled TLS Fallback SCSV: Server supports TLS Fallback SCSV TLS renegotiation: Secure session renegotiation supported TLS Compression: OpenSSL version does not support compression Rebuild with zlib1g-dev package for zlib support Heartbleed: TLSv1.3 not vulnerable to heartbleed TLSv1.2 not vulnerable to heartbleed TLSv1.1 not vulnerable to heartbleed TLSv1.0 not vulnerable to heartbleed Supported Server Cipher(s): Preferred TLSv1.3 128 bits TLS_AES_128_GCM_SHA256 Curve 25519 DHE 253 Accepted TLSv1.3 256 bits TLS_AES_256_GCM_SHA384 Curve 25519 DHE 253 Accepted TLSv1.3 256 bits TLS_CHACHA20_POLY1305_SHA256 Curve 25519 DHE 253 Preferred TLSv1.2 256 bits ECDHE-ECDSA-CHACHA20-POLY1305 Curve 25519 DHE 253 Accepted TLSv1.2 128 bits ECDHE-ECDSA-AES128-GCM-SHA256 Curve 25519 DHE 253 Accepted TLSv1.2 256 bits ECDHE-ECDSA-AES256-GCM-SHA384 Curve 25519 DHE 253 Accepted TLSv1.2 128 bits ECDHE-ECDSA-AES128-SHA Curve 25519 DHE 253 Accepted TLSv1.2 256 bits ECDHE-ECDSA-AES256-SHA Curve 25519 DHE 253 Accepted TLSv1.3 256 bits TLS_AES_256_GCM_SHA384 Curve 25519 DHE 253 Accepted TLSv1.3 256 bits TLS_CHACHA20_POLY1305_SHA256 Curve 25519 DHE 253 Preferred TLSv1.2 256 bits ECDHE-ECDSA-CHACHA20-POLY1305 Curve 25519 DHE 253 Accepted TLSv1.2 128 bits ECDHE-ECDSA-AES128-GCM-SHA256 Curve 25519 DHE 253 Accepted TLSv1.2 256 bits ECDHE-ECDSA-AES256-GCM-SHA384 Curve 25519 DHE 253 Accepted TLSv1.2 128 bits ECDHE-ECDSA-AES128-SHA Curve 25519 DHE 253 Accepted TLSv1.2 256 bits ECDHE-ECDSA-AES256-SHA Curve 25519 DHE 253 Accepted TLSv1.2 256 bits ECDHE-RSA-CHACHA20-POLY1305 Curve 25519 DHE 253 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve 25519 DHE 253 Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-GCM-SHA384 Curve 25519 DHE 253 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA Curve 25519 DHE 253 Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA Curve 25519 DHE 253 Accepted TLSv1.2 128 bits AES128-GCM-SHA256 Accepted TLSv1.2 256 bits AES256-GCM-SHA384 Accepted TLSv1.2 128 bits AES128-SHA Accepted TLSv1.2 256 bits AES256-SHA Accepted TLSv1.2 112 bits TLS_RSA_WITH_3DES_EDE_CBC_SHA Preferred TLSv1.1 128 bits ECDHE-ECDSA-AES128-SHA Curve 25519 DHE 253 Accepted TLSv1.1 256 bits ECDHE-ECDSA-AES256-SHA Curve 25519 DHE 253 Accepted TLSv1.1 128 bits ECDHE-RSA-AES128-SHA Curve 25519 DHE 253 Accepted TLSv1.1 256 bits ECDHE-RSA-AES256-SHA Curve 25519 DHE 253 Accepted TLSv1.1 128 bits AES128-SHA Accepted TLSv1.1 256 bits AES256-SHA Accepted TLSv1.1 112 bits TLS_RSA_WITH_3DES_EDE_CBC_SHA Preferred TLSv1.0 128 bits ECDHE-ECDSA-AES128-SHA Curve 25519 DHE 253 Accepted TLSv1.0 256 bits ECDHE-ECDSA-AES256-SHA Curve 25519 DHE 253 Accepted TLSv1.0 128 bits ECDHE-RSA-AES128-SHA Curve 25519 DHE 253 Accepted TLSv1.0 256 bits ECDHE-RSA-AES256-SHA Curve 25519 DHE 253 Accepted TLSv1.0 128 bits AES128-SHA Accepted TLSv1.0 256 bits AES256-SHA Accepted TLSv1.0 112 bits TLS_RSA_WITH_3DES_EDE_CBC_SHA Server Key Exchange Group(s): TLSv1.3 128 bits secp256r1 (NIST P-256) TLSv1.3 128 bits x25519 TLSv1.2 128 bits secp256r1 (NIST P-256) TLSv1.2 128 bits x25519 SSL Certificate: Signature Algorithm: sha256WithRSAEncryption ECC Curve Name: prime256v1 ECC Key Strength: 128 Subject: *.google.com Altnames: DNS:*.google.com, DNS:*.appengine.google.com, DNS:*.bdn.dev, DNS:*.cloud.google.com, DNS:*.crowdsource.google.com, DNS:*.datacompute.google.com, DN S:*.google.ca, DNS:*.google.cl, DNS:*.google.co.in, DNS:*.google.co.jp, DNS:*.google.co.uk, DNS:*.google.com.ar, DNS:*.google.com.au, DNS:*.google.com.br, DN S:*.google.com.co, DNS:*.google.com.mx, DNS:*.google.com.tr, DNS:*.google.com.vn, DNS:*.google.de, DNS:*.google.es, DNS:*.google.fr, DNS:*.google.hu, DNS:*.g oogle.it, DNS:*.google.nl, DNS:*.google.pl, DNS:*.google.pt, DNS:*.googleadapis.com, DNS:*.googleapis.cn, DNS:*.googlevideo.com, DNS:*.gstatic.cn, DNS:*.gsta tic-cn.com, DNS:*.gstaticcnapps.cn, DNS:googlecnapps.cn, DNS:*.googlecnapps.cn, DNS:googleapps-cn.com, DNS:*.googleapps-cn.com, DNS:gkecnapps.cn, DNS:*.gkecn apps.cn, DNS:googledownloads.cn, DNS:*.googledownloads.cn, DNS:recaptcha.net.cn, DNS:*.recaptcha.net.cn, DNS:widevine.cn, DNS:*.widevine.cn, DNS:ampproject.o rg.cn, DNS:*.ampproject.org.cn, DNS:ampproject.net.cn, DNS:*.ampproject.net.cn, DNS:google-analytics-cn.com, DNS:*.google-analytics-cn.com, DNS:googleadservi ces-cn.com, DNS:*.googleadservices-cn.com, DNS:googlevads-cn.com, DNS:*.googlevads-cn.com, DNS:googleapis-cn.com, DNS:*.googleapis-cn.com, DNS:googleoptimize -cn.com, DNS:*.googleoptimize-cn.com, DNS:doubleclick-cn.net, DNS:*.doubleclick-cn.net, DNS:*.fls.doubleclick-cn.net, DNS:*.g.doubleclick-cn.net, DNS:doublec lick.cn, DNS:*.doubleclick.cn, DNS:*.fls.doubleclick.cn, DNS:*.g.doubleclick.cn, DNS:dartsearch-cn.net, DNS:*.dartsearch-cn.net, DNS:googletraveladservices-c n.com, DNS:*.googletraveladservices-cn.com, DNS:googletagservices-cn.com, DNS:*.googletagservices-cn.com, DNS:googletagmanager-cn.com, DNS:*.googletagmanager -cn.com, DNS:googlesyndication-cn.com, DNS:*.googlesyndication-cn.com, DNS:*.safeframe.googlesyndication-cn.com, DNS:app-measurement-cn.com, DNS:*.app-measur ement-cn.com, DNS:gvt1-cn.com, DNS:*.gvt1-cn.com, DNS:gvt2-cn.com, DNS:*.gvt2-cn.com, DNS:2mdn-cn.net, DNS:*.2mdn-cn.net, DNS:googleflights-cn.net, DNS:*.goo gleflights-cn.net, DNS:admob-cn.com, DNS:*.admob-cn.com, DNS:*.gstatic.com, DNS:*.metric.gstatic.com, DNS:*.gvt1.com, DNS:*.gcpcdn.gvt1.com, DNS:*.gvt2.com, DNS:*.gcp.gvt2.com, DNS:*.url.google.com, DNS:*.youtube-nocookie.com, DNS:*.ytimg.com, DNS:android.com, DNS:*.android.com, DNS:*.flash.android.com, DNS:g.cn, DNS:*.g.cn, DNS:g.co, DNS:*.g.co, DNS:goo.gl, DNS:www.goo.gl, DNS:google-analytics.com, DNS:*.google-analytics.com, DNS:google.com, DNS:googlecommerce.com, DNS:*.googlecommerce.com, DNS:ggpht.cn, DNS:*.ggpht.cn, DNS:urchin.com, DNS:*.urchin.com, DNS:youtu.be, DNS:youtube.com, DNS:*.youtube.com, DNS:youtubeeducat ion.com, DNS:*.youtubeeducation.com, DNS:youtubekids.com, DNS:*.youtubekids.com, DNS:yt.be, DNS:*.yt.be, DNS:android.clients.google.com, DNS:developer.androi d.google.cn, DNS:developers.android.google.cn, DNS:source.android.google.cn Issuer: GTS CA 1C3 Not valid before: Aug 30 01:36:08 2021 GMT Not valid after: Nov 22 01:36:07 2021 GMT |
As you see, google use now tls 1.0, 1.1, 1.2 and 1.3: